
A scan of nearly one million Ethereum smart contracts has identified 34,200 vulnerable contracts that can be exploited to steal Ether, and even freeze or delete assets in contracts the attackers don’t own.
For the average user not familiar with the world of cryptocurrencies, smart contracts are a set of coded operations that get executed automatically when someone sends an input to the contract. Here’s a basic example of how a smart contract can look like:
Consider an Ethereum smart contract that is used to auction off a digital [object]. The contract has variable “x” that counts the number of bids made on the [object]. The owner may want to prolong the bidding on the object and might set up a contract condition of “x>100″ before allowing the object to be sold to the highest bidder. Once this condition is met, the smart contract automatically initiates an Ether transaction with the winner and releases a sale order for the [object].”
Smart contracts are one of the reasons why the Ethereum network and its cryptocurerncy —Ether— are so popular. Smart contracts is what powers most of today’s ICOs, but they also run various other Ethereum-based services and tools.
Smart contracts are just code
But smart contracts and are just like any other piece of code, and may sometimes contain vulnerabilities and bugs that can be exploited.
A hacker exploited one such bug in the summer of 2016 to steal over $50 million worth of Ether from TheDAO organization.
That bug prompted researchers from National University of Singapore (NUS) to start looking for bugs in Ethereum smart contracts.
In 2016, they created a tool named Oyente that could scan Ethereum smart contracts for bugs. They initially used Oyente to analyze 19,366 Ethereum smart contracts, discovering that 8,833 were vulnerable.
That research didn’t get too much media attention at the time, and the research team’s warning regarding the manner in which most smart contracts were being coded landed on deaf ears.
Parity incident triggers new research, new scan tool
However, the research team turned its attention back to scanning vulnerable Ethereum smart contracts last fall when, yet again, someone exploited a smart contract bug to mess with users’ Ether funds.
This incident happened last November when a GitHub user named Devops199 accidentally —or intentionally (we don’t know)— locked over $285 million worth of Ether inside Parity wallets using a bug he discovered.
This incident drove researchers to create a new tool for analyzing smart contracts. Named Maian, this tool can scan for more flaws and is also specialized in at-scale scanning.
The five-person team used Maian to analyze a whopping 970,898 smart contracts, with the following results, listed in the table below:
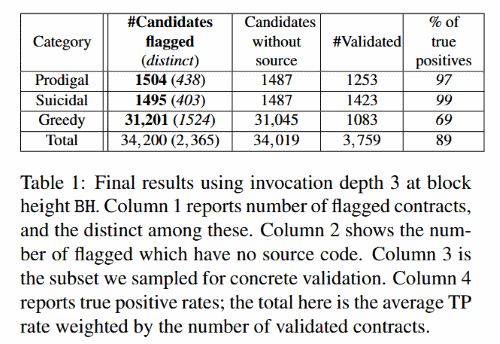
Prodigal contracts – smart contracts that when attacked send funds for safe keeping to the wrong Ethereum address (attacker’s or not).
Suicidal contracts – smart contracts that can be killed by someone else and not just the owner (Parity Devops199 bug falls here).
Greedy contracts – smart contracts that can be locked by someone else and freeze funds forever (Parity Devops199 bug also falls here).”
The results show that 3.5% of the scanned contracts are affected by a major vulnerability that can aid attackers in stealing funds or just freezing users’ Ether.
Just like in 2016, the research team is now warning users about the dangers of trusting smart contracts just a little bit too much and urges users to deploy smart contract analysis software to scan for flaws before putting their funds inside a smart contract.
Unlike in 2016, when they released the source code of Oyente, researchers have not released Maian just yet, fearing that attackers could use Maian to scan for vulnerable contracts and steal or lock up Ethereum funds.
Nonetheless, if you’re looking for a tool for scanning Ethereum smart contracts, there is also Mythril, unrelated to the NUS team’s work with Maian and Oyente. More info on the NUS team’s work is available in this research paper.
