Ledger, a company that offers cryptocurrency wallets, acknowledged on Feb 3rd that all of its hardware wallets are affected by a vulnerability which could allow a malicious third party to provide clients with false receive addresses so that crypto-currencies intended to be received by the customer would end up in an attacker’s wallet instead.
As the company says on an instructional page of its website, a “Ledger wallet generates a new address each time you want to receive a payment.”
It is in generating these addresses that this particular vulnerability comes into play.
Ledger warns that an “attacker could be in control of your computer screen and show you a wrong address which would make him/her the beneficiary [sic] of any transactions sent to it.”
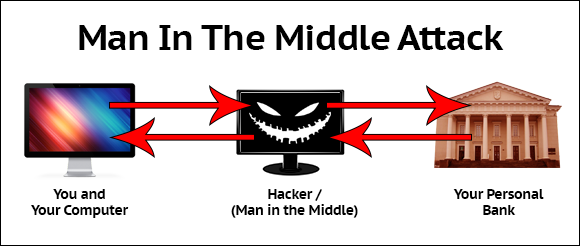
The report further explains that this is because the wallets use a “JavaScript code running on” the computer to which the device is connected. If malware capable of perpetrating a man-in-the-middle attack is present on that machine, it “can simply replace the code responsible for generating the receiving address” with code that will spit out an address belonging to the attacker.
Both the report and documentation available from Ledger Corp offer guidance on how to verify that a bitcoin receive address is correct.
The Ethereum Application has no mitigation, and the user has no way to validate if the receive address has been tampered with.” Therefore, its authors recommend that “If you’re using the Ethereum App – Treat the ledger hardware wallet the same as any other software-based wallet, and use it only on a Live CD OS that is guaranteed to be malware-free. At least until this issue receives some kind of fix.”
By the time of this publication, Ledger had not responded to a CBNN inquiry on whether this vuln threatens to affect the sending and receiving of Ether tokens as well.
A page on Ledger’s website under the header “Basic security principles” which was also updated on Feb 5th warns users that “Using a hardware wallet doesn’t make you invincible… Don’t trust, verify.”
Ledger later provided additional info on the measures it is taking to address this vulnerability.
First among them, it will add a step to the workflow of the “Ledger Wallet Bitcoin Chrome application” which encourages each user to double-check that the key on their wallet’s screen matches the one on their computer monitors.
The company is further encouraging its users “to find bugs, or security vulnerabilities,” and says in closing that “While our bounty program has not been officially launched yet, there is already a dedicated email address set up.”
